How to fix RDP: an internal error has occurred
Here are several ways to diagnose and fix the RDP: an internal error has occurred issue.

The remote desktop connection: an internal error occurred message is frustratingly general. It's a catch-all error that occurs when an RDP client cannot connect to the host due to a configuration issue. Since no additional information is provided, you may need to do some troubleshooting to find the root cause. To aid in this, we'll list the most common reasons this happens. It's likely that you'll have some idea of which are the most likely based on your actions immediately before the error occurred.
1 - Remote Desktop Connections are not allowed on the host
If you received this error the first time you tried to connect to your RDP server, this is likely the culprit. It's a common oversight, but you must enable the "allow remote connections" setting before you can RDP into a remote PC or server.
You'll find the setting on Windows 10 Pro by searching for "Remote Desktop Settings".
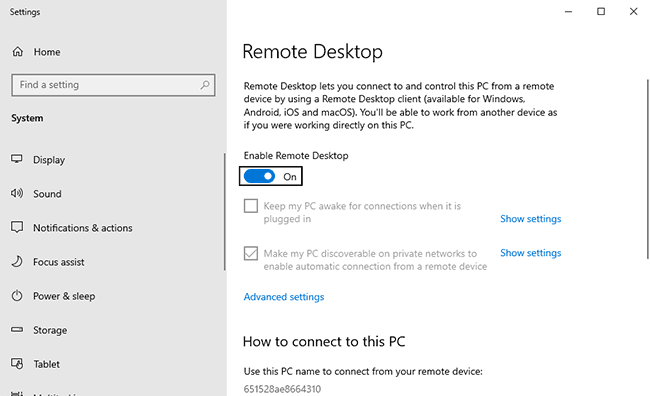
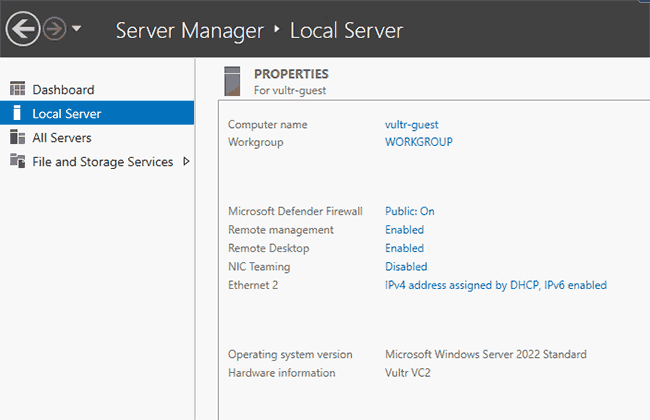
On Windows Server 2022, open the Local Server menu in Server Manager and ensure "Remote Desktop Connection" is enabled.
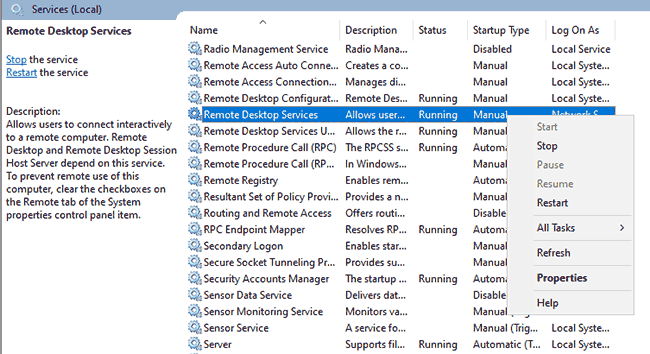
2- The Remote Desktop service has crashed
It's possible that the remote desktop service itself has stopped functioning as intended. In such cases, restarting the service can be enough to fix it. The most intuitive way to do this is via the Services app. Open it, find "Remote Desktop Services", and press "Restart".
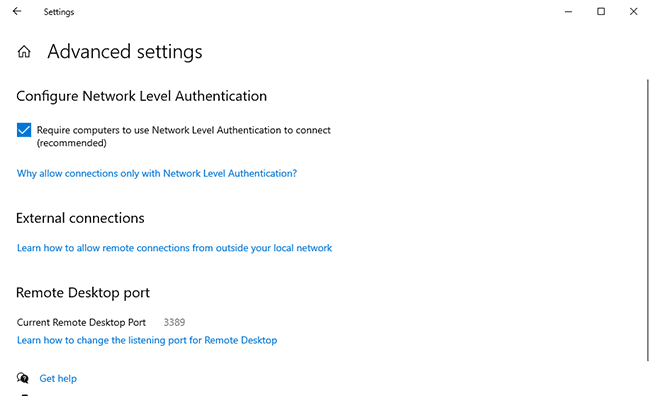
3 - Network Layer Authentication issues
The Network Level Authentication requires the client to authenticate before connecting to the host. This is an important security measure to prevent denial of service and remote code execution attacks such as BlueKeep. However, it can cause connection issues on PCs running old versions of Windows or those running RDP 6.0 or lower. Issues can also arise when connectivity is lost to a domain controller. You may want to temporarily turn off Network Layer Authentication to see whether this resolves the issue.
However, we should emphasize that this is not a permanent solution. Leaving this off can leave your server exposed to the vulnerabilities mentioned earlier. This should only be used as a troubleshooting step before you determine and fix the root cause of the NLA issue.
4 - Firewall misconfiguration
If the firewall on your server does not allow TCP traffic on your given RDP port, the connection will fail. This can happen when you change your RDP port via the registry without enabling a firewall rule first or because you accidentally blocked the wrong port.
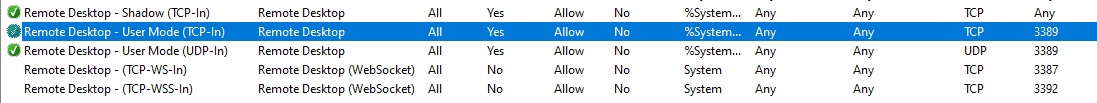
Open "Windows Defender Advanced Security" and look for "Remote Desktop" in the Inbound rules section. "Remote Desktop - User Mode (TCP-In)", should be enabled using the default RDP port, 3389. Check this port against the one listed in "Remote Desktop Settings > Advanced settings" and adjust it if needed.
5 - Proxy server issues
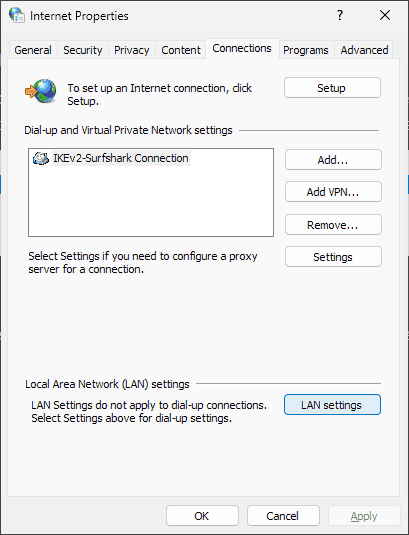
If you have a proxy server enabled on your local PC or RDP server, you may need to disable it before you can connect. This can be achieved using the Internet Options tool:
- Search for and open Internet Options
2. Open the "Connections" tab and click "LAN Settings..."
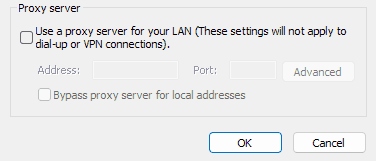
3. Untick "Use a proxy server for your LAN
4. Try connecting to your server again
If this doesn't work, try disconnecting from any Windows VPNs and trying again.
Your MTU value is too high
If you are using a VPN to connect to your RDP server (and you probably should) the default Maximum Transmission Unit value of 1500 may cause connection issues in rare cases. Cisco recommends an MTU value of 1458 on the client PC in these scenarios. You can change it with a single command in PowerShell:
netsh interface ipv4 set subinterface "Ethernet" mtu=1458
The RDP service does not run on start up
If you started to experience issues after you restarted your RDP server, check your services. It's possible that somebody mistakenly set the RDP service to not start automatically. You can check this by opening the "Services" program, double-clicking "Remote Desktop Services," and ensuring that the "Startup type" is set to "Automatic".
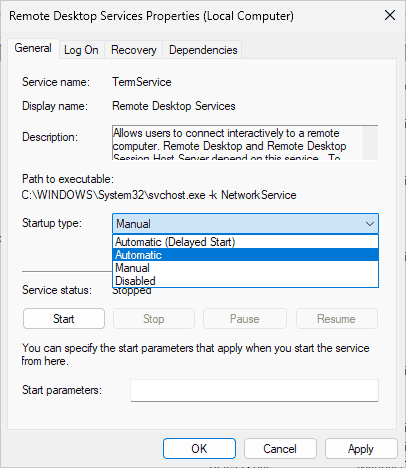
Click "Apply" and restart the server.
DDoS or brute force attacks
The default RDP port of 3389 is a common target for brute force attacks. Bots may try to log in thousands of times, trying to guess the RDP password. This high number of login requests can naturally cause issues. You can check for failed login attempts in the Event Viewer to confirm this. Just open the "Security" heading and sort by event ID. The ID 4625 signifies failed login attempts.
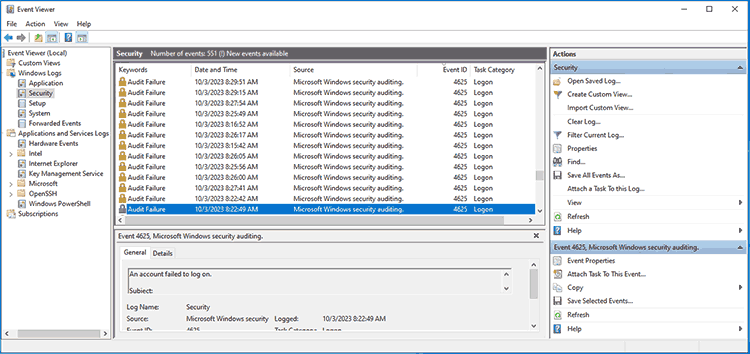
If you do not have many attempts but suspect an intentional DDoS attack, install software such as Wireguard to monitor your traffic.
If you find signs of an attack, do not worry -- it is easy enough to mitigate. Changing your RDP port will significantly reduce the number of automated login attempts, or you can restrict RDP access to specific IP addresses.